Get a global view of your external attack surface, including supply chain, with mapped assets, subdomains, and real-time risk insights
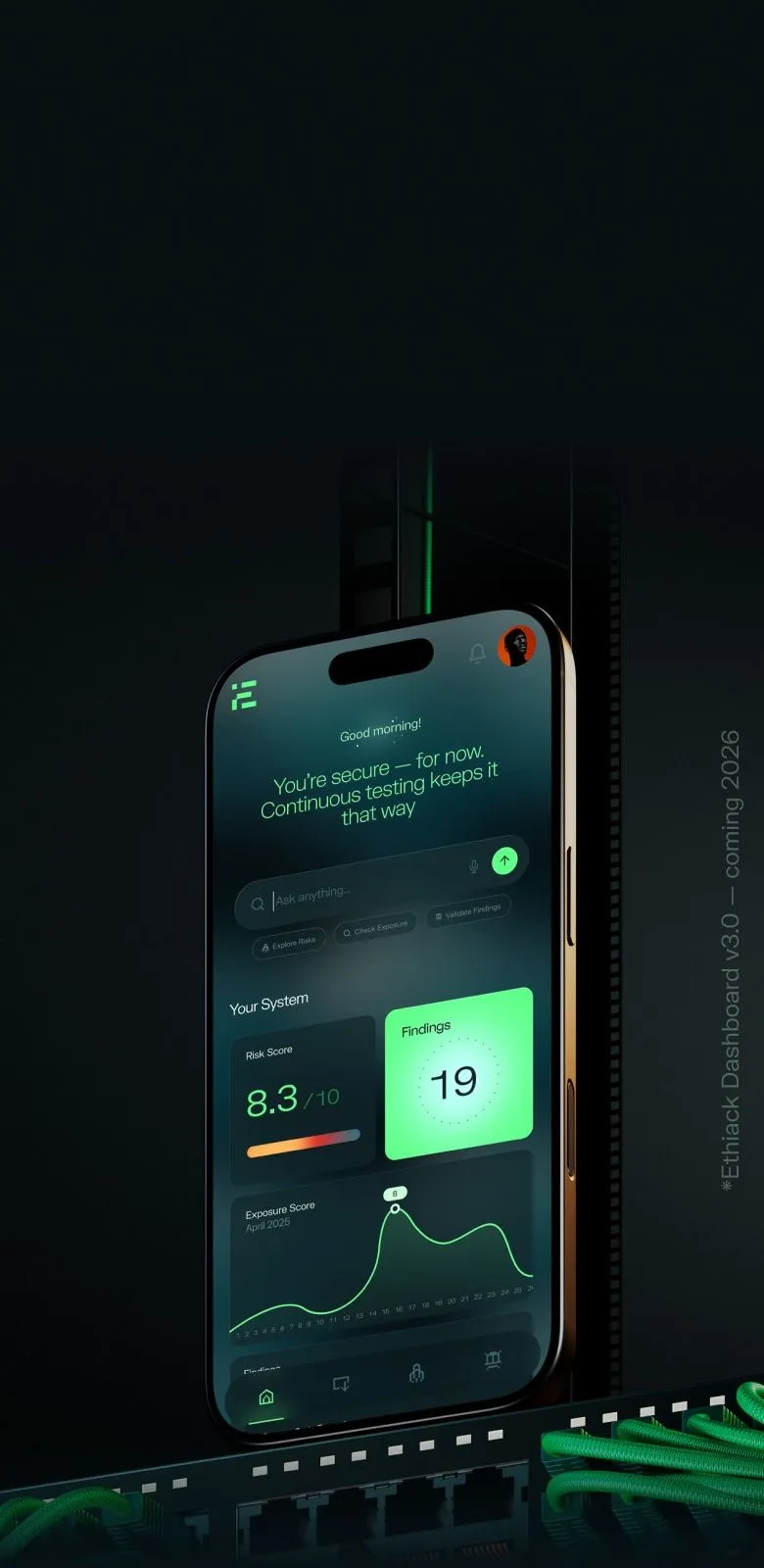
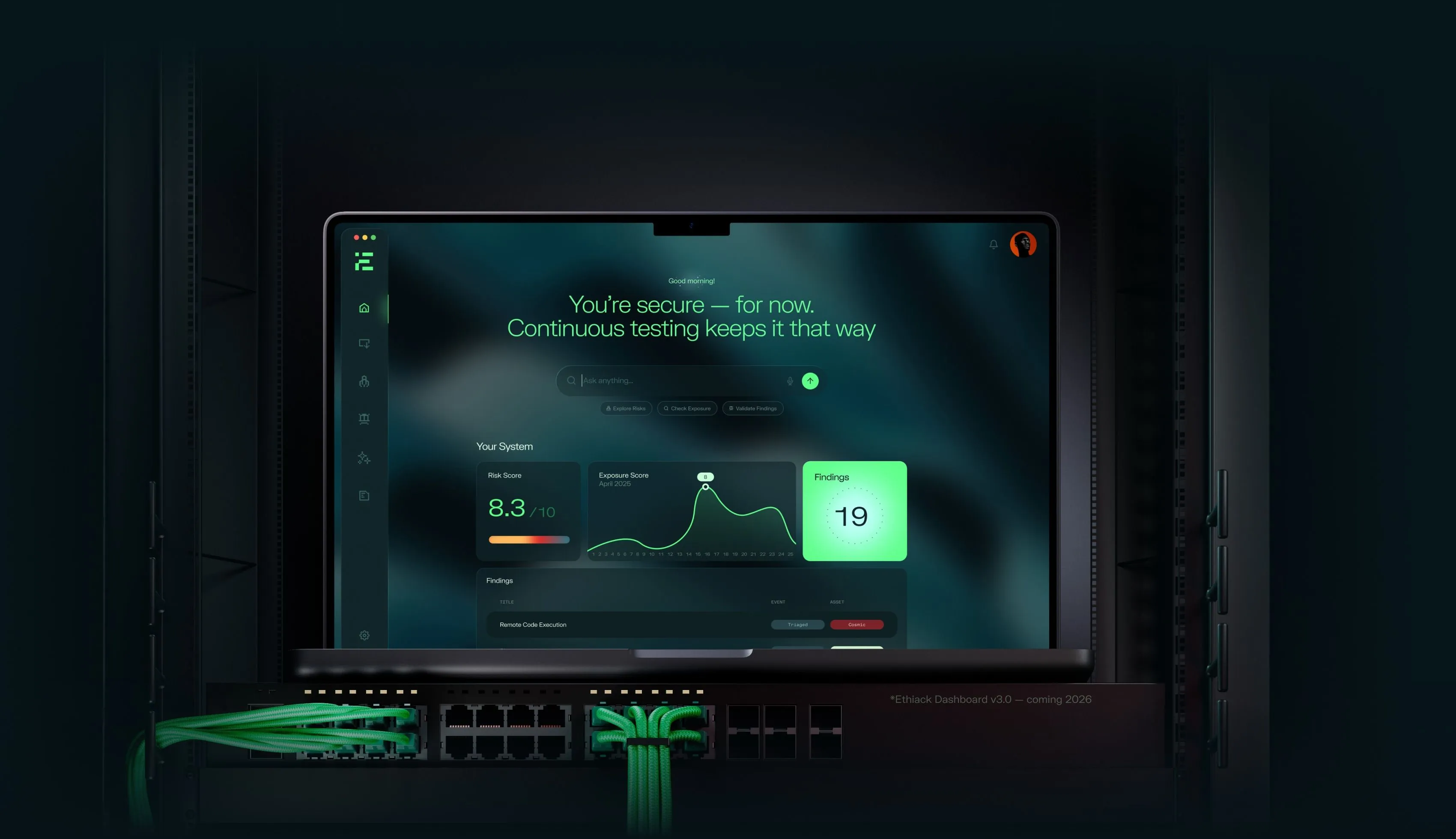
Autonomous Ethical Hacking for continuous security
Ethiack combines AI-powered pentesting with expert insight to continuously uncover, validate and prioritize real risks. Act fast and reduce exposure, 24/7.
Ethiack is leading the future of proactive cybersecurity.
We blend AI-powered pentesting agents with the creativity and diligence of ethical hackers to help companies stay ahead of threats — not just react to them.
Meet
Combining AI Speed with Human Precision for the highest level of Security.
The
Hackian

Agentic AI pentesting
- Pentest
External Assets
- Pentest
Internal Network Environments
Ethiack Beacon automates internal asset pentesting. Any detected change triggers a new test — complementing ongoing black-box and grey-box testing of your external assets
- Pentest
Mobile Assets
We cover key attack vectors, from authentication to cloud integrations, and validate vulnerabilities that pose real risk
- SoonPentest
Cloud
Support seamless integration with cloud platforms
- Pentest
Authentication
Test assets with user credentials using a grey-box methodology
- Pentest
Credentials
Identify exposed credentials and breach-related dumps
The issues of today
Traditional scanners create too much noise and flag too many false positives. Traditional Pentests are not frequent enough.
Our solution
Our AI pentesting agents, Hackians, deliver both frequency and depth to solve these issues.
- over
99.5%
Accuracy in Finding Exploitable Vulnerabilities
- Over
+100k
Vulnerabilities Identified with Proof-of Concept Exploit
- Over
75%
PortSwigger Labs solved
- Over
200
Different Classes of Vulnerabilities Covered (AKA CWEs)
- Over
30 X
Times Faster Than a Manual Pentest
Stay secure with Ethiack
SeeTestAct
- .01
See
Complete visibility of your attack surface and supply chain with continuous attack surface management.
Complete visibility of your entire attack surface — external, internal and third-party assets
Find Hidden Risks — map every asset to discover and secure unknown assets and shadow IT
Live evolving map — always up-to-date, no blind spots
Internal & external assets
Third‑party & supply chain
Diverse assets: mobile, IoT, OT, cloud
- .02
Test
Hackian doesn’t wait for an annual pentest, it continuously tests, exploits, and validates vulnerabilities with the speed of AI and the creativity of human hackers.
Continuous Testing — autonomous, event-driven testing (on code pushes, infrastructure changes, new knowledge)
Speed & Scale — execute thousands of attack scenarios in minutes
Proactive Discovery — finds novel vulnerabilities before criminals do
Rapid discovery of vulnerabilities
Testing triggered by code changes or events
Lead in finding new, emerging threats
- .03
Act
Actionable risks and compliance-ready reporting. We validate every finding with proof-of-exploitation, so your team can focus and act on the vulnerabilities that matter.
Validated Exploitable Findings — no more time wasted with noise or false positives
Prioritized Risks — get mitigation steps and guidance on what to fix first
Compliance Ready — pull live reports for ISO, SOC2, PCI and DORA
Accuracy + exploitability + impact
Proof‑of‑exploit & clear remediation guides
Compliance reporting & real‑world risk scores
Want to know more about the pricing?
Get your quote here
Values & Essence
Built on Transparency, Ethics, Synergy and Trust (T.E.S.T.)
We hack to protect, combining the speed of AI with human creativity, so you can secure what truly matters.
- T.
Transparency, with customers, colleagues, and hackers
We believe in openness.
We're honest, critical, and relentless in our pursuit of security.
While we'll never promise 100% security, we'll always ensure our customers are resilient by having a crystal-clear understanding of their risks and how to mitigate them. And we're committed to fairly rewarding security researchers for their invaluable contributions.
- E.
Ethics, at the heart of our work
Ethics isn't just part of our name; it's in our code. We hack with integrity. We test to protect.
Ethiack combines "Ethics" and "Hack" for a reason: we deeply respect privacy, confidentiality, and impact. Our work is rigorous, our people are vetted, and our standards are non-negotiable.
- S.
Sinergy, because security is collaborative
Security is a team sport.
We are committed to providing the most advanced proactive security testing. But, true prevention happens when machines and humans work together to continuously uncover actionable risks — but our customers complete the cycle. What we find, their teams mitigate.
We're all in this together.
- T.
Trust, is what matters after all
Ultimately, trust is everything. Ethiack is built by people, for people.
Customers trust us with their digital assets. Ethical hackers trust us with their skills. Employees trust us with their careers, and investors trust us with their capital. In return, we deliver consistently, with responsibility and excellence. We don’t know everything, but we always learn. So, we trust you to make vital contributions that help us build a more secure digital world.
Ready to Transform Your Security?
Stop Hoping, Start Knowing
- Matteo Penzo
As the CEO of Zick learn, I believe it's my role to make our company secure, not just today, but also tomorrow and the day after tomorrow. We treat a lot of client data, and protection is part of the product. Ethiack makes it possible for us to offer maximum security on every layer.
- André Araújo
The way Ethiack incorporates EASM with Automated Pentesting has brought us simplicity and proactivity in solving large-scale problems. As a group with so many exposed assets, doing this work manually was simply impossible. The main transformation was the gaining a complete view on our surface, which we previously lacked. What we have publicly exposed, their vulnerabilities, and our impact in the cyberspace.
- João Annes
Ethiack's combination of automated testing and human expertise brought a unique perspective to our security challenges. Their continuous monitoring of our attack surface and in-depth manual testing of our internal systems have transformed how we approach cybersecurity. Ethiack teaches us to think like attackers, making us better equipped to handle threats proactively.
- Paulo Ribeiro
We can sleep better at night knowing that if something shows up, we'll know right away.




